New features in 1.8.0#
This documentation applies to Piler enterprise edition 1.8.0
Revision #2
Publication date: Oct 5, 2024
Reworked the GUI using bootstrap 5.3 and vue.js 3#
Modernized the GUI using the latest bootstrap and vue.js. The new GUI is responsive, supports mobile devices, and finally we have dark mode as well.
Better CSS customization#
You can easily override any CSS formatting, eg. change colours, font types, etc.
To do that add the following to /etc/piler/config-site.php:
$config['CUSTOM_CSS'] = '<link rel="stylesheet" href="/assets/css/my.css">';
Then add your CSS definitions to /var/piler/www/assets/css/my.css file.
You may use your own images, favicons, etc. as well. Feel free to customize the following variables, then write them to config-site.php:
$config['TOAST_LOGO'] = '/assets/images/logo-round.svg';
$config['SITE_LOGO'] = '/assets/images/login-logo.svg';
$config['BRANDING_LOGO'] = '/assets/images/logo-header.svg';
$config['NOT_FOUND_404_IMAGE'] = '/assets/images/404.svg';
$config['PLACEHOLDER_IMAGE'] = '/assets/images/50x50.png';
$config['PLACEHOLDER_ZIP'] = '/assets/misc/1.zip';
$config['PLACEHOLDER_PDF'] = '/assets/misc/1.pdf';
$config['REMOTE_IMAGE_REPLACEMENT'] = '/assets/images/remote.gif';
$config['BRANDING_FAVICON'] = '
<link rel="apple-touch-icon" sizes="180x180" href="/assets/ico/apple-touch-icon.png">
<link rel="icon" type="image/png" sizes="32x32" href="/assets/ico/favicon-32x32.png">
<link rel="icon" type="image/png" sizes="16x16" href="/assets/ico/favicon-16x16.png">
<link rel="manifest" href="/assets/ico/site.webmanifest">
<link rel="mask-icon" href="/assets/ico/safari-pinned-tab.svg" color="#5bbad5">
<link rel="shortcut icon" href="/assets/ico/favicon.ico">
<meta name="msapplication-TileColor" content="#da532c">
<meta name="msapplication-config" content="/assets/ico/browserconfig.xml">
<meta name="theme-color" content="#ffffff">
';
$config['BRANDING_URL'] = ''; // the URL when hovering over the logo
Inactivity timeouts#
The GUI automatically logs the current user out after 1 hour inactivity. Also the user's session expires and thus forces a logout after 2 hours.
These are both configurable variables, set the following in /etc/piler/config-site.php, and fix the values to your needs:
$config['$ESSION_INACTIVITY_TIMEOUT'] = 3600;
$config['SESSION_EXPIRY_TIMEOUT'] = 7200;
Cloudflare Turnstile#
Added support for Cloudflare Turnstile, a smart captcha alternative, with much better user experience. From their website:
"Turnstile delivers frustration-free, CAPTCHA-free web experiences to website visitors - with just a simple snippet of free code. Moreover, Turnstile stops abuse and confirms visitors are real without the data privacy concerns or awful user experience of CAPTCHAs."
See https://www.cloudflare.com/products/turnstile/ for more.
After registering a free account at Cloudflare, you may setup Turnstile. Then add the following variables to /etc/piler/config-site.php (be sure to use your values):
$config['CF_TURNSTILE_SITEKEY'] = '0x4AAAAAAAXXXX-XXXXXXXX';
$config['CF_TURNSTILE_SECRET'] = '0x4AAAAAAAXXXXYYYYYYYYYYYYYYYYY';
Authentication against Keycloak#
See https://mailpiler.com/keycloak-authentication/ for the details how to setup.
Authentication against OKTA oidc#
See https://mailpiler.com/okta-oidc-authentication/ for the details how to setup.
Authentication against linkedin#
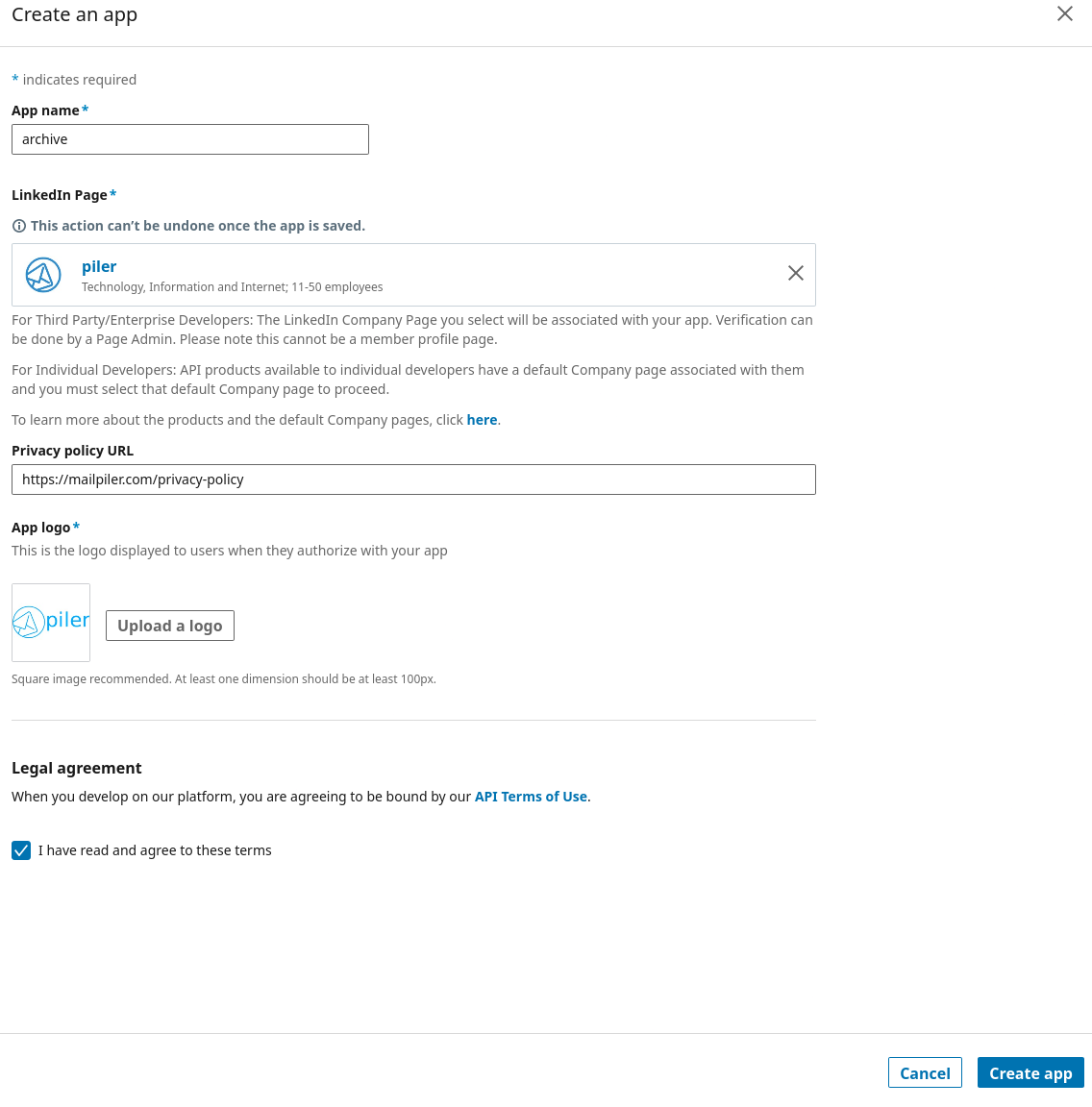
Visit https://developer.linkedin.com/ and create an app.
You need a company linkedin page, a logo, and preferably a link to your privacy policy. Accept the legal agreement, then click "Create app"
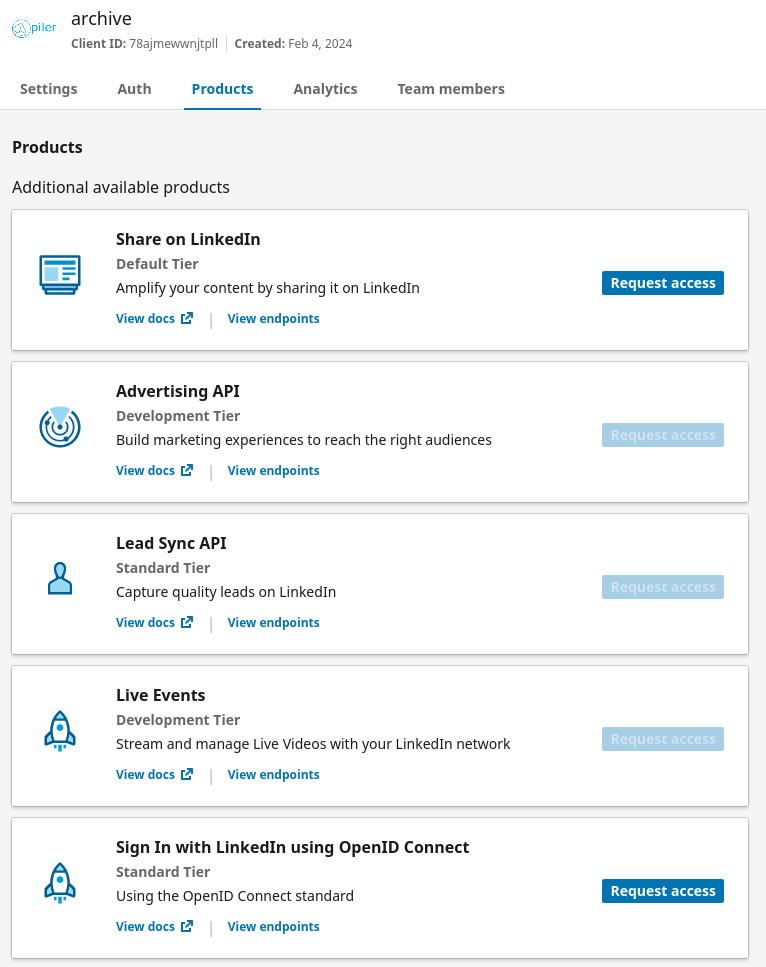
On the "Products" page locate the "Sign In with LinkedIn using OpenID connect" product, then click on the "Request access" button.
Finally on the "Auth" tab locate the "Authorized redirect URLs for you app" settings, and type https://archive.example.com/callback-linkedin (be sure to use your archive's URL).
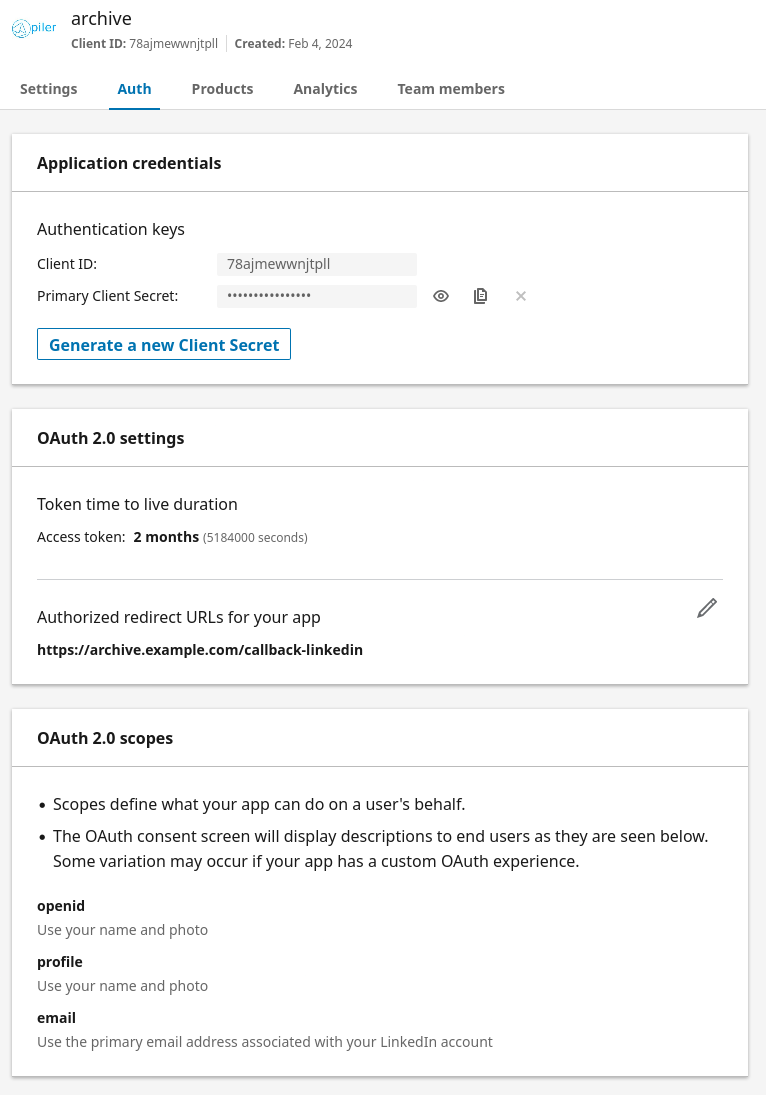
Edit /etc/piler/config-site.php, and add the following. Use your client id and secret values.
$config['ENABLE_LINKEDIN'] = 1;
$config['LINKEDIN_CLIENT_ID'] = 'xxxxxxxxxxxxx';
$config['LINKEDIN_CLIENT_SECRET'] = 'yyyyyyyyyyyyyy';
$config['LINKEDIN_REDIRECT_URI'] = 'https://archive.example.com/callback-linkedin';
Exporting huge number of emails from the archive#
See https://mailpiler.com/exporting-emails/ for the details how to setup and use.